KSG Recommendations for a Controlled Shutdown of Russian Operations
State of Play, Ukraine Crisis
Russia’s invasion of Ukraine has triggered not only devastation and a humanitarian crisis within Ukraine, but also a rapidly deteriorating political and economic situation within Russia itself.
Tensions will only continue to mount: any company with on-going operations in Russia will face critical decision points in the next 24-72 hours. Executives considering a Russian exit must act now to protect their people and assets in the region:
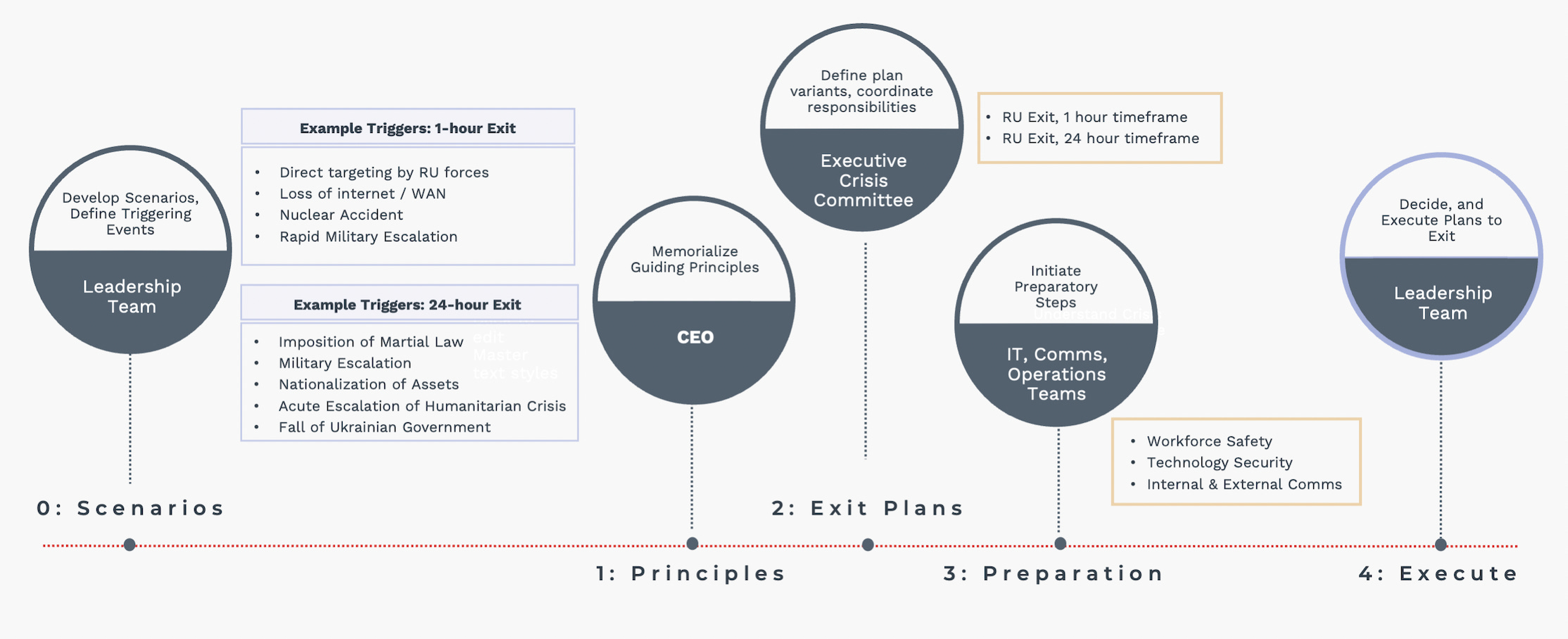
Executive Level Process for a Controlled Exit
0: Consider Scenarios for Exit: firmly decide what scenarios will trigger your organization.
1: Determine Guiding Principles: anchor critical decisions in your organization’s core values.
2: Executive Committee to Create Exit Plan: determine 24hr and 1hr guidelines.
3: Operational Teams to Begin Preparation: prepare and take all actions short of beginning the exit plans.
4: Execute your Exit: act swiftly and decisively.
Extenuating circumstances may require your organization to remain in Russia, in the short- or long term, but KSG has advised its clients who are able to exit the country to do so as soon as possible. This advisory is meant for the executive team of multinational corporations with relatively minor operations remaining in Russia. If your organization has a more significant presence—facilities, factories, IP, or large numbers of employees—in the region, or faces other extenuating circumstances, additional preparation will be necessary immediately.
We should note that any exit from Russia may be in violation of current or future Russian law (and that future laws may be enforced retroactively), nothing in this advisory constitutes legal advice, and you should include legal counsel in all planning, decision-making, and implementation.
0: Potential Scenarios and Triggers for Exit
Executives at organizations that have not yet decided to leave must firmly decide what events will trigger an exit. Given what has occurred in this crisis over the past 72 hours, the following situations should be especially considered:
Scenarios Potentially Triggering a 24hr Exit:
Imposition of Martial Law: curfews, restrictions on the movement of people and goods, and crackdowns on interactions with external organizations are likely under consideration in Moscow.
In the last 24 hours, Russian officials adopted heavy & retroactive criminal penalties for disseminating information about the invasion of Ukraine counter-official state narratives.
Communications with or from locally employed staff are unlikely to be exempted, internal corporate communications if reported could be subject to prosecution.
Soviet-style restrictions on the emigration of Russian citizens appear increasingly likely.
Nationalization of Foreign-Held Assets, which senior Russian officials have threatened in retaliation for western sanctions. Abrupt moves to divest from or exit the Russian market—particularly in key economic sectors like oil and gas—are likely to draw scrutiny and perhaps trigger seizure of assets.
Continued Escalation in Ukraine into Humanitarian Crisis: including the use of chemical weapons, targeting aid routes and infrastructure, and disregard for innocent life.
The decisive fall of Ukrainian Government, likely sparking a prolonged and destructive insurgency; leaving the Ukrainian economy in tatters; and bringing sanctions on the remaining occupying forces and Moscow-installed leaders.
Scenarios Potentially Triggering a 1hr Exit:
Direct targeting of US or Russian Staff by Russian Security Services: arrests or detentions, or any event which jeopardizes employee safety should trigger withdrawal. These risks include employees joining or being implicated in opposition or protest movements in Russia.
Loss of Internet/WAN connectivity: western providers have already begun to reduce internet and WAN transit into Russia, potentially cutting off employees from information and additional aid. Consider encrypted emergency communication back-up channels to activate now.
Nuclear accident: though Chernobyl is often mentioned, Ukraine’s four active nuclear power plants are also at stake, and the world has already witnessed an attack on one plant. Deliberate or inadvertent military strikes or significant power outages could have catastrophic impacts and warrant significant safety concerns.
Urgent Military Escalation: including incursions by Belarusian or Russian forces into NATO countries or accidental exchanges with NATO, Swedish, or Finnish forces.
1: Your Organization’s Guiding Principles for Action
Ensuring alignment between your organization’s values and its actions during a time of crisis will be extremely challenging given competing pressures and rapidly changing conditions on the ground. Organizations are under intense scrutiny for their actions from all quarters—governments both foreign and domestic, shareholders, competitors, the global public, and most importantly their own employees.
All are examining the key decisions and ethical choices that organizational leaders make during these incidents, the results of which can have far-reaching impacts on organizational brand, finances, and culture. The safest course of action is to anchor critical decisions in an organization’s stated core values. Decisions ahead are fraught with potentially conflicting imperatives and tensions across issues of safety, security, reputation, competition, and profit/loss.
Memorialize your organization’s guiding principles in descending order. Use your list as the basis for prioritizing activities, selecting responsible courses of action, and driving your internal and external communications strategies.
Suggested Guiding Principles:
Act in a manner consistent with the ethical and moral framework of your company, treating employees with respect and empathy.
Use your power to reduce risks to personal safety and well-being for employees, whenever possible.
Double-check instincts and maintain a sense of objectivity as the crisis unfolds; emphasize measured judgement.
Manage cyber risk to your company in line with other guiding principles, including accepting some temporary friction in key business processes to get your Shields Up.
Consider steps you can take to protect customers, clients, and partners, in addition to those that protect your own enterprise and people.
Public relations and reputational risk are likely elevated for your organization. Take steps to manage this risk in a way that reinforces the guiding principles above but never at the expense of ethical action or the protection of individuals. The best public relations plan is to act in an ethical manner.
2: Executive Committee Creates Exit Plans – 24hr, 1hr
The moment your organization decides to exit Russia will be abrupt – a plan for action at such an event must be created today. This plan should prioritize securing your organization’s people, critical assets, and critical IP, in a manner guided by your organization’s goals above.
In the scenarios mentioned above, your organization can reasonably expect 24hrs for a complete exit. In the case of direct targeting by Russian entities, such as detention of your employees by Russian government officials, you will need to minimize loss in a 1hr window or less. Both 24hr and 1hr plans should include several key components of an exit strategy:
IT/Security: To include data retention/deletion, access management, email retention (more details below).
Human Resources: To include development of exit paperwork, employee notifications, and post-severance engagement.
Communications and Customer Support: To include preparation of key messaging, designation of trusted spokesperson(s), notifications to customers in-country and externally.
3: Operational Teams Begin Preparations
It will be difficult to reverse course once your organization initiates the execution of an exit plan. As your executive team finalizes exit preparations, operational partners across IT, HR, Comms, and additional areas of the organization should act now to prepare for and minimize loss in case of rapid escalations.
A detailed list of technical preparation and shutdown steps that your organization’s IT and security teams can begin with immediately is detailed below. HR, Comms, and related teams will be critical for ensuring workforce safety. These teams should coordinate with the crisis response function in your organization, and take immediate preparatory actions including:
Localize and maintain consistent contact via secure channels with your teams in Russia, Ukraine, and broader Eastern Europe, with a focus on their individual safety.
Alert your organization to avoid attributing public statements in support of Ukraine to Russian employees or offices, as this might heighten the personal risk of those employees.
Transfer monies into the affected regions to support severance payments and other shutdown costs, in compliance with sanctions.
Review supplier information, to include vendor agreements and contracts to identify potential legal risks or issues and prepare any required mitigation.
Ensure sufficient staffing is in place across the relevant business operations functions and ready for rapid activation at any hour to support exit tasks.
4. Execute your Exit
Once the decision has been made to exit, organizations must act swiftly yet deliberately to ensure an orderly and effective withdrawal. During this time, executive-level coordination—including all relevant organizational leadership—is especially critical to ensuring efficiency, rapid and informed decision-making, and consistent public and employee messaging. Use checklists or other task tracking tools to ensure activities are comprehensive, properly sequenced, and tracked to completion. Establish a regular cadence of leadership coordination meetings to ensure closeout activities are being performed, revise elements of the plan as needed, and rapidly resolve issues as they emerge.
The critical component of a successful exit is to act decisively—the choices and steps to exit can be costly and painful, yet timely, ethical decision-making is critical given the speed with which action is necessary in these circumstances.
Recommend Technical Steps for Exit
Technical Preparation Steps
KSG recommends that these preparatory steps be implemented immediately as the decision to exit is considered. None of these precautions should commit the company to a course of action but are necessary to execute a controlled withdrawal.
Provision access for out-of-country admins – Many large enterprises use local staff to administer in-country endpoints or even entire domains. Creating and testing the proper access for administrators outside of Russia is a critical first step.
Test or deploy backup VPN access – Major international bandwidth providers are already shutting down links into Russia, and backup site-to-site client-server VPNs will be necessary to allow access into Russian corporate networks.
Create groups/OUs for in-country employees and service accounts – Not all organizations will start this process with groups or organization units that allow the deployment of the controls necessary for shutdown.
Perform a system and data inventory – Perform network scanning, examination of switch/Wi-Fi logs, DHCP logs and an inventory of running services to try to determine the location of:
Shadow IT
Critical intellectual property stored physically on Russian servers
Customer data
Non-Russian PII
Begin backing up data to the cloud or out-of-region datacenters – While WAN links are still operational, it is important to export all critical in-country data to cloud or other external hosts. It should be noted that doing so might violate Russian law, which is likely to be a minor consideration for most companies at this point, so it is important that this step not include any participation by Russian nationals.
Physical servers (file level)
Virtual servers (snapshots)
Laptops/desktops (critical folders)
Deploy volume- and folder-level encryption on high-risk servers – If you are not ready to wipe in-country resources, then deploying volume-level encryption (with keying material stored out of country and entered using console servers or IPMI) is a good step to maintain some control, even if contact with your servers is lost. Folder level encryption can be used if necessary but provides less assurance without detailed audits of data location.
Crash deploy data-loss prevention (DLP) and/or endpoint detection and response (EDR) products – If you do not already have a deep understanding of process execution, file access, and USB device use on your servers and endpoints in region, then crash-deploying an agent could be a useful step. Note that most of these agents now use cloud management that will become useless if Russia is blocked from major cloud providers.
Move most RU office internet transit to the WAN – To avoid cloud access being intermediated by Russia’s new deep packet inspection capabilities deployed on the public internet, swing internet transit routes to terminate in a European PoP via your WAN. This step will have the added benefit of running internet traffic past NIDS/netflow systems deployed outside of Russia. Be careful not to make this change for the DMZ hosting your backup VPN.
Implement email retention policies – Companies want to retain email communication with their employees as long as possible, but access to years of documents and emails should be restricted to prevent exfiltration.
Office365 customers should refer to this Microsoft Docs space, which provides a step-by-step guidance to customize an archive and deletion policy for mailboxes in your organization.
Gather alternative contact information for Russian employees – Companies may want to continue communication with Russian employees to discuss HR issues (such as severance) and for humanitarian support, but doing so after shutting down an office will be difficult. Gathering up personal emails (preferably hosted on Russian webmail providers, as access to Gmail is likely to be restricted) and non-corporate phone/text numbers is one option.
Technical Shutdown Steps
These steps should be considered for inclusion in both the 24hr and 1hr plans.
Deactivate in-country administrative access – This step is critical, but also might tip-off your Russian IT staff and could pose a point-of-no-return on exiting the country.
Review identity provider policies and configuration looking for staff who may have the ability to modify roles, groups, and access. Pay particular attention to team members with access to reset passwords, unlock user accounts, and configure application access. Do this for both on-premise and hosted identity stores.
Remove access to those team members who can control building access, as those systems can provide physical access to critical systems found in server rooms, or controlled access.
If your organization uses a colocation provider in region, revoke access to request access and disable accounts in any available portals.
Implement blocking DLP policies – At this point, you should also turn up blocking DLP policies to the maximum extent to prevent exfiltration of corporate IP or PII.
Begin wiping high-risk internal servers – High-traffic servers, NAS, and SAN devices hosted in region cannot realistically be surveyed for all critical data and will need to be encrypted and/or wiped remotely.
NAS Filers can often be encrypted at the volume level and shutdown remotely.
SAN volumes can be encrypted and then deleted.
Windows servers can be encrypted with Bitlocker and off-device keying material added as required using manage-bde. This will allow for the protection of data using remote desktop or PowerShell.
Encrypt then destroy RAID volumes for servers and systems where specific controllers are used.
Deprovision access to intranet services – Eliminate access to internally hosted services using Layer-7 access control mechanisms.
Deprovision access to cloud services – Eliminate access to SaaS and other cloud services at a group level.
Lock/wipe endpoint PCs as appropriate – Companies might decide to allow employees to keep corporate mobile devices and laptops for humanitarian reasons (practically, getting hardware out of Russia has become extremely difficult and legally risky for Russians). Devices should, at a minimum be locked remotely, and if possible they should be wiped and returned to a no-OS or pre-setup mode.
Intune users can securely return a Bitlocker encrypted Windows machine to an out-of-box experience (OOBE).
Deprovision mobile devices – Likewise, companies might decide to allow mobile devices to stay with their ex-employees, but such devices should be deprovisioned and removed from MDM once local corporate apps are deleted.
Lock user accounts – User accounts should be locked in the corporate identity management system. Deleting accounts often causes data loss and should not be performed at this time.
Cut WAN access, maintaining a VPN backup – Finally, eliminate all Layer-3 communication via the WAN at a firewall or router outside of Russia. While you can keep the WAN link active for contingencies, you should assume that any live connections could be used as an entry point to your network.
KSG team members Isabella Garcia-Camargo, Micah McCutchan, Bill Moore, Sean Feeney and Gavin Wilde contributed to this advisory.