KSG ExecBrief: Navigating the AI Risk Landscape
Generative AI Use-Cases: Discovering, Monitoring, and Controlling Risk
Insight
How will enterprise AI development and consumption change corporate governance, risk, and compliance responsibilities?
To finish up our series on AI, we’ll leave you with a snapshot of how KSG is currently advising our clients on Generative AI Risk Management. This isn’t a dogmatic blueprint or a master plan—it’s a starting point to drive immediate, tactical actions that minimize risk while maximizing optionality to capture efficiencies from innovation.
We tell our clients to focus on six areas of AI risk management: 1) Regulatory & Compliance, 2) Technology & Security, 3) Data & Privacy, 4) Reputational, 5) Legal, 6) Operational Disruption. Orgs that already have good cross-functional teams to coordinate infosec, legal, and enterprise technology responsibilities are well positioned to manage AI integration.
An area of common challenge, however, is the relationship between AI development engineers, product managers, trust & safety, and infosec teams. It’s not clear who owns, for example, model poisoning/injection attacks, prompt abuse, or corporate data controls, among other emerging AI security challenges. Further, the shifting landscape of third-party platform integrations, open-source proliferation, and DIY capability sets hinder technology planning, security roadmaps, and budgets.
Generative AI Risks to Enterprise Consumers
Most firms will find themselves at the far end of the AI value chain, consuming third-party AI products and/or internally developed capabilities. Critical risks here encompass the obvious data confidentiality breaches, but also less appreciated upstream license/ToS/IP violation risks, trust & safety issues, and potential operational disruptions from premature business-critical integrations. See here for some examples:
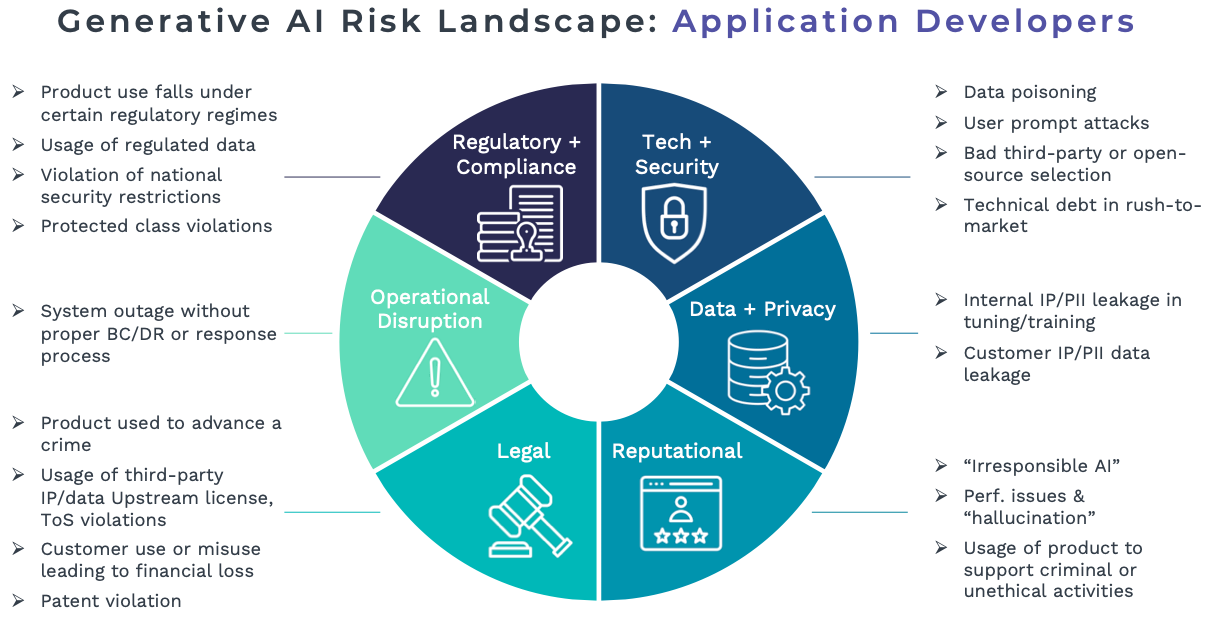
Risks from Enterprise AI Development
Very few firms will be willing or able to train their own foundation models, but many will want to fine-tune state-of-the-art LLMs and custom develop their own applications. The risk surface varies widely by industry and use-case, but novel pitfalls emerge when these applications (which may be quite powerful) are not properly tested or secured. Current DevSecOps methodologies will need to be significantly adapted and expanded to fit the use-case, regulatory, and security paradigm of each firm. Consult this chart for some specific risk examples:
Use-Case Discovery, Monitoring, and Control
We are advising our clients to take a crawl, walk, run approach (correlated to their broader Don’t Go, Go Slow, or YOLO AI strategy). This starts by conducting an inventory of current and anticipated use-cases. Already we’ve seen enterprises consider: local training/usage & inference, information retrieval, writing assistance (multi-language), code review & generation, contract review & generation, document and template creation, business intelligence, financial projection & modeling, data analysis, marketing & advertising copy/imagery, work product design, corporate communications, customer support, and more.
Getting visibility and oversight of these proliferating use-cases and applications is critical. Firms must then put in place a comprehensive and dynamic risk governance, monitoring and control system to assess and mitigate security and compliance risks. This will require increased cross-functional collaboration as well as flexible business processes, analytics, and technical tooling (much of which is still nascent and rapidly evolving).
Some firms have taken these initial steps. Many have not. Those that delay will find themselves behind their peers, rushing to catch up, and exposed to increased security and liability risks. It’s best to start now.
For more information or assistance on these issues, please reach out to intel@ks.group.
Forwarded this ExecBrief by a friend? Click below to sign up for our weekly dispatch.
Global Scan
Geopolitics
Global Supply Chains Have Recovered, although Inflation Remains High: The Economist reports that supply chains have returned to pre-pandemic levels of stress and capacity. Energy price spikes and other disruptions have nevertheless kept costs elevated.
Germany Faces Tough Five Year Ahead: The economic engine of the European Union risks slowing, economy minister Robert Habeck warned in response to an International Monetary Fund report predicting Germany’s GDP will shrink by 0.3 percentage points this year. Habeck urged electricity price caps and energy subsidies to hold industry over.
US Looks to Latin America to Diversify Chip Supply Chain: The governments of Panama and Costa Rica have both expressed willingness to partner with the United States on repackaging and shipping, with help from Chips Act subsidies.
Cybersecurity
Researchers Find Encryption Backdoor in Radios Used by Police, Industry: Voice radio protocol used to transmit encrypted data and commands in pipelines, railways, electrical grids, mass transit, and freight trains has carried the flaw for over two decades.
US, Australian Governments Issue Advisory on IDOR Vulnerability: Insecure direct object references (IDORs), allow hackers to access or modify sensitive data. servers because of a lack of proper security checks. In recent years, medical, municipal, tax, education, mortgage, and geolocation data have all been exposed as a result.
Strategic and Emerging Technology
New Electric Motor Cuts Need for Rare Earths: Japanese metal maker Proterial has advanced a new prototype motor for electric vehicles that uses magnets made with ferrite, rather than neodymium – the most common type currently used in electric vehicles, and mainly sourced from China.
Intel CEO Promises AI in “Every Product We Build”: The pledge comes as Intel follows Apple, AMD, and Qualcomm in shipping its first consumer chip with a built-in neural processor for machine learning tasks, later this year.
UFO Reports Demand Greater Transparency, Lawmakers Say: A former US intelligence officer alleged to Congress that rogue special access programs have captured and attempted to reverse engineer “non-human intelligence”-related technology for decades. Sponsored by Leader Schumer and the Select Committee on Intelligence, the Senate has added extensive UAP provisions to the annual defense and intel authorization bills to mitigate “potential technological surprise”.
Policy/Regulation
US Securities and Exchange Commission Adopts Cyber Breach Disclosure Rule: Publicly traded companies will be required to report “material” breaches within four days after the determination has been made – and routinely update on their risk governance and cyber expertise.
European Council Advances $47 Billion Chips Act: The legislation is aimed at spurring the continent’s semiconductor industry through subsidies, investments, and research and development—and to double the EU’s global market share to 20% by 2030.
Major AI Companies Commit to White House Proposed Safeguards: The tech firms agreed to eight measures, including independent testing of models, cybersecurity, sharing trust & safety findings, and watermarking synthetically generated content.